2014-09-04
Guide to Remove Backdoor.Ratenjay!gen3 Easily from Your Computer
If your computer is infected with Backdoor.Ratenjay!gen3, you should remove it immedaitely. read this post, you can get more information about the Trojan and as well as the removal guide.
Backdoor.Ratenjay!gen3 is a dangerous Trojan horse which can infiltrate computers around the world. It can sneak into all versions of Windows including Windows Vista, Windows 7 and Windows 8. Once installed, Backdoor.Ratenjay!gen3can hooked deeply into the background system. It can block some basic operating programs, delete important files and occupy highly CPU. You will notice that your computer runs in a very slow speed and sometimes stuck.
How to Remove HackTool:Win32/Keygen Easily from Your Computer
Brief Introduction about HackTool:Win32/Keygen
HackTool:Win32/Keygen is a dangerous Trojan horse which can sneak into all versions of Windows including Windows Vista, Windows 7 and Windows 8. Once installed, HackTool:Win32/Keygen will change the computer setting by modifying the registry entries and start up items. When you starts the computer, it will rum itself automatically at the background. By taking up a lot of system resources and occupy high CPU, your computer performance will be very slow.
How to Remove Web Optimizer Safely and Absolutely
My computer got infected with Web Optimizer. Is it a virus? It is annoying and I am really afraid. How can I remove it from my computer? No worries, Here in the post you can find the removal guide.
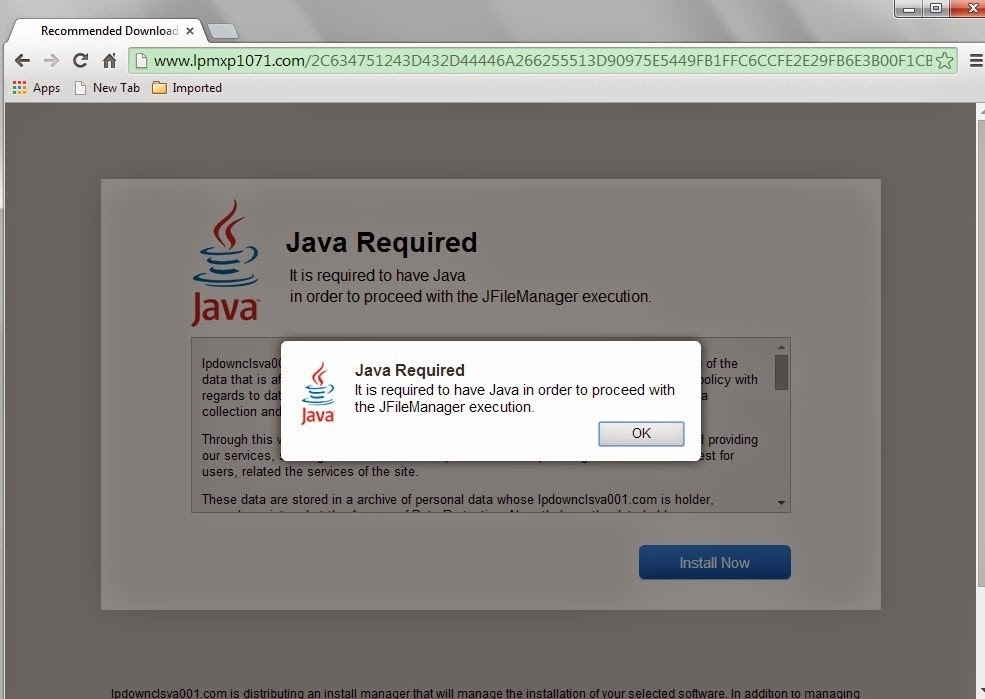
How to Remove Lpmxp1071.com - Removal Tips
My browser infected with Lpmxp1071.com. It always pop ups on my browser. I try to remove it but fail. Can anybody tell me how to do? No worries, Here in the post you can find the removal guide.
Screenshot of Lpmxp1071.com
How to Remove Cryptographic Locker Completely
Brief Introduction about Cryptographic Locker
Cryptographic Locker is a dangerous ransomware which is similar to Cryptolocker. It has the ability to encrypt your files stored on the target computer including including .txt, .jpg, .doc, .adb, .cmt, .cib. This ransomware can infiltrates the target computer with infected file sharing network, corrupted free programs, malicious links, spam email attachments, malicious secondary storage devices, unauthorized website and so on.
